- Who are we?
Strategic IT partner
Count on our expertise to accelerate your digitisation
- Maximum partnerships with A+ brands
- Mountains of experience in thousands of environments
- Unrivalled expertise in cybersecurity
- Up to 24/7 monitoring & support
- Core healthy business for +30 years
- +200 Certified employees with passion
- Sober, knowledgeable advice
- Unique puzzle of proven top solutions
From advice until installation, from support until complete relief.
We are ready! - Managed Services
IT Analyses, Consulting, installations...
- NIS-2 Cybersecurity AuditCertified experts uncover every vulnerability
- Applications (Dynamics 365 ERP/CRM, Microsoft 365, Copilot...)Work more efficiently (together) with Dynamics 365 & Microsoft 365, among others
- Licence Audit (Software Asset Management)Are all licences in order? You can often optimise and save a lot!
- General IT Analysis and InstallationsA new look at your environment by our specialists
- Wi-Fi SurveyDetect and fix jammers and hard-to-reach areas
- Solutions
- Events
Accelerate your digitalization.
Get an interactive tour of state-of-the art solutions. - Jobs
Join our team from Turnhout, Houthalen and/or Geel.
You end up in a 'Great Place To Work!'From advice until installation, from support until complete relief.
We are ready! - Customer Area
As a customer, you can manage support tickets, quotes and licences yourself.
Request access via business@vanroey.beNeed a login or request a quote? Contact us via internalsales@vanroey.be | 014 470 600
Storm-2372 'Device code phishing' attack
Our support will regularly inform you of important events here.
The cyber threat group 'Storm-2372′ has been carrying out attacks on governments, NGOs and various industries worldwide since August 2024, abusing 'Device Code Phishing' where an access token is misused.
Storm-2372 'Device code phishing' attack
The group uses a technique called device code phishing, tricking victims into signing up to fake login pages, stealing their authentication tokens. This enables attackers to gain access to their accounts and data, and even make lateral movements within networks.
Recently, Microsoft adopted that the group is now also abusing the Microsoft Authentication Broker to refine their attack techniques and maintain longer-term access.
How does device code phishing work?
It is a way to extract your access token and abuse it afterwards.
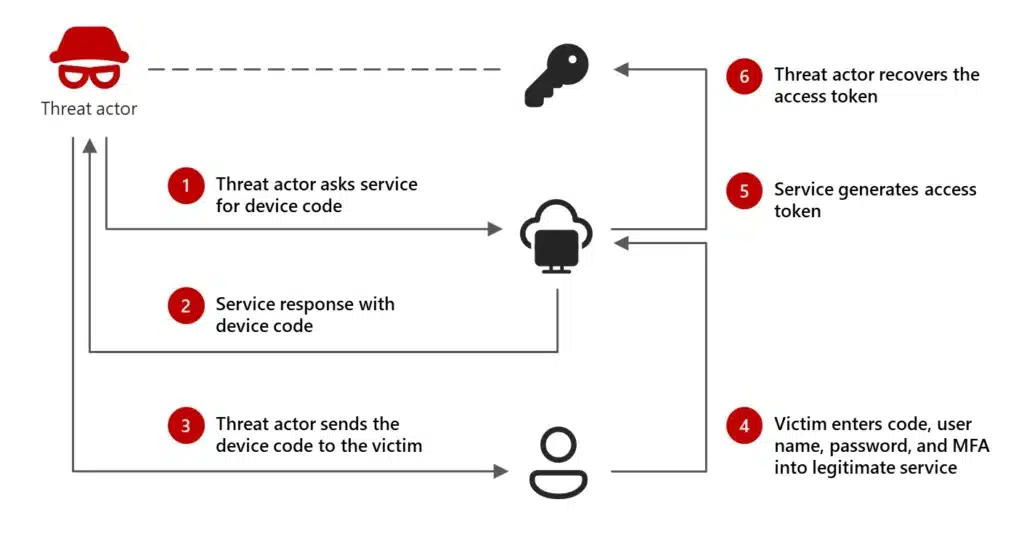
What is VanRoey doing to prevent this in your area?
Customers who use our Managed Microsoft 365 services enjoy are already extra well protected anyway thanks to the strict policies we enforce. For example, we restrict who can add devices to Entra ID and limit the validity of sessions. But we are also taking additional measures:
- We are pushing an additional Conditional Access policy to all Managed customers to prevent this attack.
- We also strongly recommend the User Awareness (KnowBe4) training to prevent phishing in its broadest sense
What can you do yourself to prevent this?
To prevent this threat, it is initially crucial to make users aware of phishing techniques and suspicious login requests by using a 'Security Awareness campaign‘.
Organisations can mitigate the risk by reducing the device code authentication flow eliminate where possible and a strict Conditional access policy set up. It also recommends making multifactor authentication (MFA) mandatory and giving preference to phishing-resistant methods such as FIDO tokens or Microsoft Authenticator with passkeys. Also blocking legacy authentication and regular monitoring of suspicious login activity can help detect attacks early.
Take action
In addition to the aforementioned User Awareness training and tightening/enforcing the right policies in your Microsoft 365 environment can be found in the source article more information as well as options to maximise protection.
Should suspicious behaviour be observed, it is important to immediately contact the refresh tokens of affected accounts and require users to log in again. Implementing a sign-in risk policy can help to automatically respond to suspicious logins.
Finally, it is recommended to centralise identity and access management to detect suspicious activity faster and strengthen the organisation's security.
Feel free to contact us to minimise this risk for you. Existing customers can get a create a ticket. Others feel free to send an email at support@vanroey.be or count: 014 470 600.
Can't create tickets? Ask here to get an account. If our Engineer needs to remotely control your PC, he or she will ask you to run this software .




