Operational Technology: from CNC machine to nuclear power plant
Industrial Control Systems (ICS), such as SCADA and PLC controls, used to be isolated silos where cybersecurity was not considered. But attacks on OT can lead to serious consequences, ranging from reduced productivity to physical accidents or even social disasters. Thinking about the hack at the Colonial Pipeline in the US, which caused a fuel shortage, or attacks on nuclear power plants in Iran... The potential consequences are incalculable.
Today, for example, there is ransomware that specifically targets CNC machines. Nothing immediately seems wrong, but once you start production, the values deviate slightly from the input time after time and the whole production process is disrupted. Hackers also eagerly exploit less secure OT environments to find their way into the rest of the corporate network.
LAT relationship for IT & OT
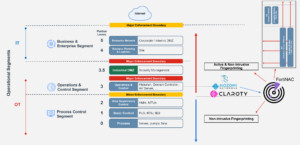
Therefore, zone '3.5', a Industrial DMZ between OT and IT, implemented adding security management and specific scanning protocols. Fortinet offers various solutions and collaborates with specialised partners in the OT landscape for this purpose, such as Dragos, Nozomi, Microsoft, Siemens, Schneider Electric etc... to ensure the most adequate security.
NAC & Deep Packet inspection for Operational Technology
It is important to keep the O of OT in mind at all times. So security measures should not get in the way or cause unnecessary disruption to the production or operation of your organisation.
This is how a NAC with DPI (Network Access Control with Deep Packet Inspection) system differently at OT. You want to avoid a device being accidentally barred from the network, because that impact is much more dramatic than if, for example, a printer is momentarily inactive. The type of traffic as well as the protocols also differ from traditional IT traffic. That is why we work with active, non-intrusive device classification & fingerprinting.
On some 20 levels (think mac-address + https requests + Vendor logo + tcp requests...) a profile of devices is set up and 'rogue devices' can be detected immediately and you can decide automatically or manually what to do with them. Because Fortinet also opens up its ecosystem to third-party integration, it can communicate directly with systems from Modbus, Siemens, Microsoft and numerous other specialists to correctly process this information and protocols at all times.
Application Control
With Application Control, operational operation is further analysed and secured. The system knows and studies the usual operation of your devices thanks to the aforementioned integration with partners. If certain commands come in with expected values between e.g. 0 and 2, there is no problem, but as soon as an unexpected value would appear, alarm bells go off.
Industrial honeypot

In conclusion
It is important to regularly monitor and update the security of OT systems. Many OT systems are still running on older software versions, such as Windows XP, which are no longer supported, so extra care should be taken to ensure these systems remain compliant with the latest security standards.
This article is only a summary of this video presentation by Lars Putteneers, Channel System Engineer at Fortinet. In it, he goes much deeper into the PERDUE model, as well as the challenges and solutions involved in today's OT environment.
Security audit for your Operational Technology environment?
Want to know how safe your environment is? You can rely on our thorough Security audit, where our experts will test your environment for more than 60,000 attack vectors and come and make a physical visit. All issues will come to the surface. Want to know more? Then feel free to request some additional info:
VAT no.
share this post:










