Social engineering
Technique in which a hacker, or social engineer, manipulates people to make them perform certain actions or disclose confidential information. There are various forms of social engineering, such as phishing, tailgating, baiting, vishing and so on.
Phishing
When a hacker tries to trick you via email so that you disclose sensitive information or take a certain action that could be dangerous to yourself or your organisation (e.g. clicking on a link, downloading an infected attachment). A phishing email often asks you to perform an urgent action. This is because hackers want to create a sense of urgency so that you react quickly and make the wrong choice.
Spear phishing
A form of phishing that is more targeted at a specific person or organisation. The hacker first researches his or her target, and then persuades the victim to perform a potentially dangerous action in the most specific and personal way possible.
Vishing
Vishing, or voice phishing, is a technique in which a hacker tries to reach his or her victims by phone. By coming across as credible as possible, the hacker aims to trick you into revealing confidential information to him or her.
Smishing
Smishing, also known as SMS phishing, is a form of phishing where the hacker tries to trick you via text messages.
Consent phishing
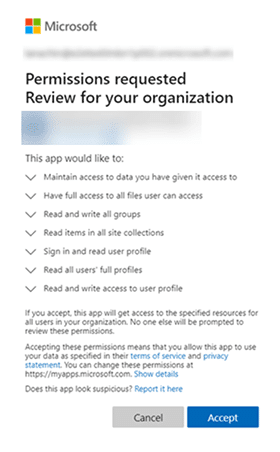
Tailgating
Tactic where a social engineer tries to gain physical access to your organisation, for example by using tricks to follow an employee inside. For example, he can pretend to work in your company or pretend to come to deliver something. By staying close behind the authorised person, the hacker can easily get past physical access controls. He can also force the employee to open a door, for example.
Pretexting
Technique in which a social engineer lies to obtain private data. Through a fabricated story, he or she tries to gain your trust so that you give the information the hacker wants. For example, the hacker may also pretend to be another person, such as an IT employee or an auditor.
Baiting
Baiting is a social engineering technique where tangible items are used, such as a USB stick. The hacker programs the USB stick so that when it is used, it creates a connection between the user's device and the hacker's device, and all data is collected and transmitted. The USB stick need only be left in an office, reception area, car park and so on, for a curious user to notice it and want to know what is on it.
Do you still have a question or want more information about our security approach? Then be sure to contact us, our consultants will be happy to help!
share this post:









