An extra layer of protection
Traditional security technologies, such as antispam, web filtering, IPS, antivirus, app control and IP reputation techniques, are necessary protections. But they will not stop today's most advanced attacks. This is because their operation is based on identifying known attack indicators.
So the danger arises when an attack is brand new or can mask itself through tunneling, encryption or other avoidance methods. If you add sandboxing to your security strategy, then you add an extra protection layer please. And one that can detect malicious code, even if it was previously unknown.
Simulate control systems
When there is a suspicious bag in the airport, the first thing to do is to cordon off the surrounding area and send a de-mining robot to open the bag so that - regardless of what happens - no victims can fall.
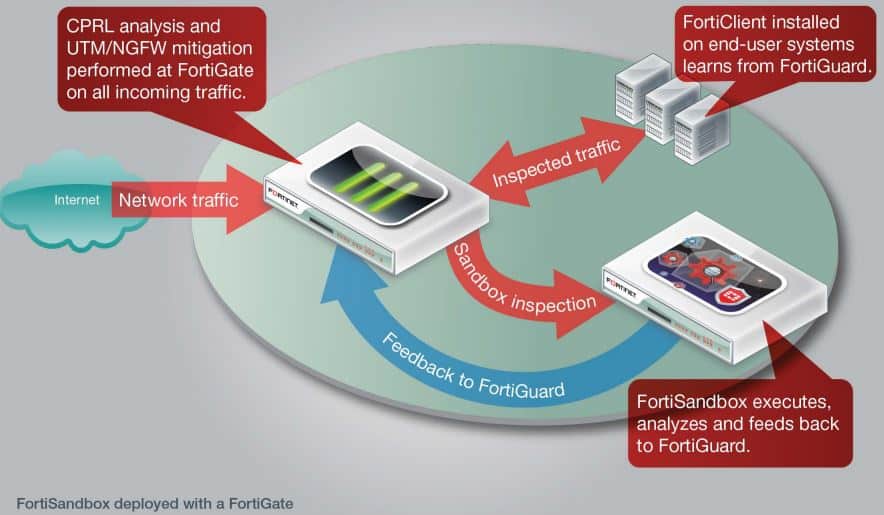
A sandbox works in a similar way. It simulates the environment and behaviour of real end-user systems. A new, 100% shielded environment is set up and the - potentially malicious - code is extensively executed and tested. Even before the suspicious file appears in your mailbox, the system will first open that file in a protected environment and extensively analyze what it does exactly.
To assess malware, sandboxes will have multiple code evaluation processes with different operating systems and technologies. The unknown code is, as it were, being played with in the sandbox. FortiSandbox gives priority to different code evaluation processes depending on the extent to which malware occurs in different configurations. In this way, the process is considerably accelerated.
FortiSandbox offers optimal security in combination with the established Fortinet security toolssuch as a FortiGate Next Generation Firewall (NGFW), FortiEDR and FortiMail.
FortiSandbox performs better thanks to CPRL
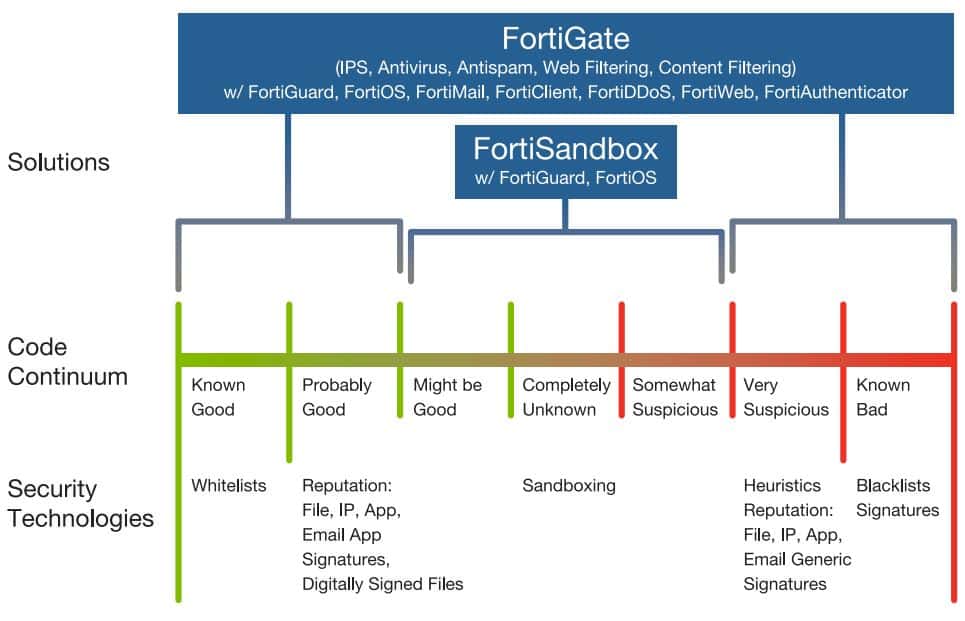
Fortinet uses Compact Pattern Recognition Language (CPRL). This is a patented technology, developed by FortiGuard Labs, for performing a very deep code inspection. CPRL can Identify 50,000 disguisesused by known malware.
If CPRL detects a known avoidance technique, FortiGate can block the code immediately, without sending it to the sandbox. In this way, the sandbox is less burdened and can reserve all its resources to work on code that is still unknown.
Sandboxing works with your existing security tools
Antispam, IPS, antivirus, web filteringIP reputation, firewalls, secure e-mail gateways and EDR... Sandboxing does not replace these security tools. Your sandbox must work with them to provide an additional layer of protection that can be managed as part of a comprehensive defense.
 Advantages of FortiSandbox
Advantages of FortiSandbox
- Prevents breaches by advanced, as yet unknown attacks
- Identifies unknown malware
- Blocks more spearphishing attacks
- Increase the effectiveness of your NGFW, UTM or Secure Email Gateway solution
share this post: